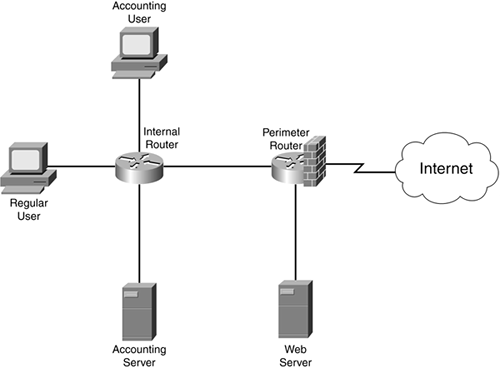
VPN is an encrypted connection between
private networks over a public network such as the Internet. There are two types of VPN: Site to Site VPN and remote VPN.
Site to Site VPN
This allows computers at fixed locations to establish secure connections with each other over a public network such as the internet. This is like creating a tunnel and extending the network by making resources from one location available at other locations. There are 2 types of Site to Site VPN: Intranet-based, and Extranet-based.
Intranet-based
It is when there are one or more remote locations that wish to join in a single private network, they can create an intranet VPN to connect each separate LAN to a single WAN.
Extranet-based
Extranet-based is like connecting LANs together. This extranet VPN allows different intranet to work together in a secure, shared network environment while preventing access to their separate intranets.
Remote VPN
This VPN secures connections for remote users to corporate LANs over shared service provider networks. There are 2 components required in this type of VPN: Network Access Server(media gateway or remote access server), and client software.
Client software
This software is require for people who wants to use VPN from their computers. This is needed to establish and maintain a connection to the VPN.The client software sets up the tunnelled connection to a NAS, which the user indicates by its Internet address. The software also manages the encryption required to keep the connection secure.
REFERENCE: lecture slide
IMAGE: http://www.google.com.sg/imgres?um=1&hl=en&sa=N&biw=1366&bih=643&tbm=isch&tbnid=5PCiajLCLnlbIM:&imgrefurl=http://techeric.com/Eric-Ortiz/portfolio.html&docid=h09FmOyr6VvGJM&imgurl=http://techeric.com/Eric-Ortiz/Images/Network/Diagrams/Site-to-Site%252520VPN.jpg&w=995&h=655&ei=EE3KT6vaHM_OrQe5sLDVDg&zoom=1&iact=hc&vpx=558&vpy=189&dur=2668&hovh=182&hovw=277&tx=133&ty=149&sig=106332796734911297201&page=1&tbnh=119&tbnw=181&start=0&ndsp=18&ved=1t:429,r:2,s:0,i:88
http://www.google.com.sg/imgres?um=1&hl=en&sa=N&biw=1366&bih=600&tbm=isch&tbnid=GHPPHjbujcBtQM:&imgrefurl=http://www.infotecs.biz/vpn-remote-access.htm&docid=yZ5wWooZCgg41M&imgurl=http://www.infotecs.biz/i/vpn-remote-access.jpg&w=698&h=582&ei=pU7KT_CrFsW4rAf3t9HMDg&zoom=1&iact=hc&vpx=496&vpy=138&dur=2944&hovh=205&hovw=246&tx=137&ty=76&sig=106332796734911297201&page=1&tbnh=123&tbnw=148&start=0&ndsp=18&ved=1t:429,r:2,s:0,i:74
http://www.google.com.sg/imgres?um=1&hl=en&sa=N&biw=1366&bih=600&tbm=isch&tbnid=GHPPHjbujcBtQM:&imgrefurl=http://www.infotecs.biz/vpn-remote-access.htm&docid=yZ5wWooZCgg41M&imgurl=http://www.infotecs.biz/i/vpn-remote-access.jpg&w=698&h=582&ei=pU7KT_CrFsW4rAf3t9HMDg&zoom=1&iact=hc&vpx=496&vpy=138&dur=2944&hovh=205&hovw=246&tx=137&ty=76&sig=106332796734911297201&page=1&tbnh=123&tbnw=148&start=0&ndsp=18&ved=1t:429,r:2,s:0,i:74