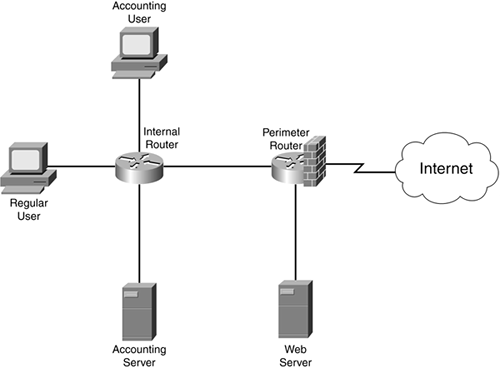
Perimeter router is placed at the Demilitarize zone, connecting the public network and the internal network. The perimeter router would help filter the outside(public network) traffic. As the Perimeter router is often connected to a slower WAN interface, it wouldn't normally provide routing functions for the internal network.

Internal Router is placed in the internal network, linking all the internal servers and the users in the private network.
Firewall is used to help secure a network, controlling the incoming and outgoing network traffic by analyzing the data packets and determining whether the packets are allowed. It is usually between the private and public network. There are two types of firewall: hardware based, or software based.

These three hardware can be used in different network topology and can all be in the same network topology.
Standalone perimeter router topology
This topology only uses the perimeter router connecting the public(untrusted) network to the private(trusted) network. This is the most minimal protection and usually used by small businesses and organizations.
Perimeter router,Internal router & Firewall topology
This topology uses all the 3 hardware mentioned above. It gives better and greater network performance and protection, this is usually used by big or medium business and organizations. It also have greater routing options.
Another special thing that we can look into is the perimeter router which is with a integrated firewall. This have a greater protection than just the router itself and better interoperability.
REFERENCE : http://www.ciscoarticles.com/CCSP-Cisco-Certified-Security-Professional/Perimeter-Router-Networks.html
http://en.wikipedia.org/wiki/Firewall_(computing)
IMAGE : http://www.google.com.sg/imgresum=1&hl=en&biw=1366&bih=600&tbm=isch&tbnid=
agVEpo7l8PpRvM:&imgrefurl=http://etutorials.org/Networking/Router%2Bfirewall%2Bsecurity/Part%2BIII%2BNonstateful%2BFiltering%2BTechnologies/Chapter%2B6.%2BAccess%2BList%2BIntroduction/Access%2BList%2BOverview/&docid=HC1sbrJB9jk1OM&imgurl=http://etutorials.org/shared/images/tutorials/tutorial_56/06fig01.gif&w=500&h=368&ei=qWlTGeEsm4rAfSxdHpAQ&zoom=1&iact=hc&vpx=310&vpy=53&dur=492&hovh=148&hovw=201&tx=141&ty=84&sig=114794691512992017059&page=1&tbnh=125&tbnw=170&start=0&ndsp=18&ved=1t:429,r:1,s:0,i:71
http://seann.herdejurgen.com/resume/samag.com/html/v10/i07/a6_f1.gif
http://www.google.com.sg/imgres?imgurl=http://upload.wikimedia.org/wikipedia/commons/thumb/5/5b/Firewall.png/300px-Firewall.png&imgrefurl=http://en.wikipedia.org/wiki/Firewall_(computing)&h=165&w=300&sz=30&tbnid=whJj0ztPL2e06M:&tbnh=59&tbnw=108&zoom=1&docid=Ue-U2v_FoVqaqM&sa=X&ei=WnKlT-j3A4LjrAfHmKWCAg&ved=0CJsBEPUBMAI&dur=2231
http://en.wikipedia.org/wiki/Firewall_(computing)
IMAGE : http://www.google.com.sg/imgresum=1&hl=en&biw=1366&bih=600&tbm=isch&tbnid=
agVEpo7l8PpRvM:&imgrefurl=http://etutorials.org/Networking/Router%2Bfirewall%2Bsecurity/Part%2BIII%2BNonstateful%2BFiltering%2BTechnologies/Chapter%2B6.%2BAccess%2BList%2BIntroduction/Access%2BList%2BOverview/&docid=HC1sbrJB9jk1OM&imgurl=http://etutorials.org/shared/images/tutorials/tutorial_56/06fig01.gif&w=500&h=368&ei=qWlTGeEsm4rAfSxdHpAQ&zoom=1&iact=hc&vpx=310&vpy=53&dur=492&hovh=148&hovw=201&tx=141&ty=84&sig=114794691512992017059&page=1&tbnh=125&tbnw=170&start=0&ndsp=18&ved=1t:429,r:1,s:0,i:71
http://seann.herdejurgen.com/resume/samag.com/html/v10/i07/a6_f1.gif
http://www.google.com.sg/imgres?imgurl=http://upload.wikimedia.org/wikipedia/commons/thumb/5/5b/Firewall.png/300px-Firewall.png&imgrefurl=http://en.wikipedia.org/wiki/Firewall_(computing)&h=165&w=300&sz=30&tbnid=whJj0ztPL2e06M:&tbnh=59&tbnw=108&zoom=1&docid=Ue-U2v_FoVqaqM&sa=X&ei=WnKlT-j3A4LjrAfHmKWCAg&ved=0CJsBEPUBMAI&dur=2231
Nice tutorial. I have the basic information regarding this topic. But you explained in a very effective way by showing the diagrams. I recall all the things but now in very clear way.Thanks.
ReplyDeletedigital signature